| Add_workflow_for_techpubs |
|---|
| AUTH1 | UserResourceIdentifier{userKey=8a00a0c85b2726c2015b58aa779d0003, userName='null'} |
|---|
| JIRAIDAUTH | SYM-2302224331 |
|---|
| REV5 | UserResourceIdentifier{userKey=8a00a0c85b2726c2015b58aa779d0003, userName='null'} |
|---|
| REV6 | UserResourceIdentifier{userKey=8a00a0c85b2726c2015b58aa779d0003, userName='null'} |
|---|
| REV3 | REV1 |
|---|
|
| UserResourceIdentifier{userKey=8a00a02355cd1c2f0155cd26cd700a1f, userName='null'} |
|---|
| REV1 | UserResourceIdentifier{userKey=8a00a02355cd1c2f0155cd26cc5207f0, userName='null'} |
|---|
|
| Warning |
|---|
|
| Warning |
|---|
| title | READ BEFORE BEGINNING |
|---|
|
You must follow these steps completely and in the order shown. Failure to do so increases the risk of node failure. |
| Note |
|---|
SBC Edge now supports a new deployment with CCE 2.1.0 in release 7.0.1. Before this release, if your CCE auto-updates to CCE 2.1.0: - To rerun the step “Transfer Credential from SBC”, it will require 7.0.1.
|
This page provides a step-by-step procedure This page provides a step-by-step procedure for Non High Availability Deployment on SBC Edge CCE.
| Multiexcerpt |
|---|
| MultiExcerptName | BeforeYouStart |
|---|
|
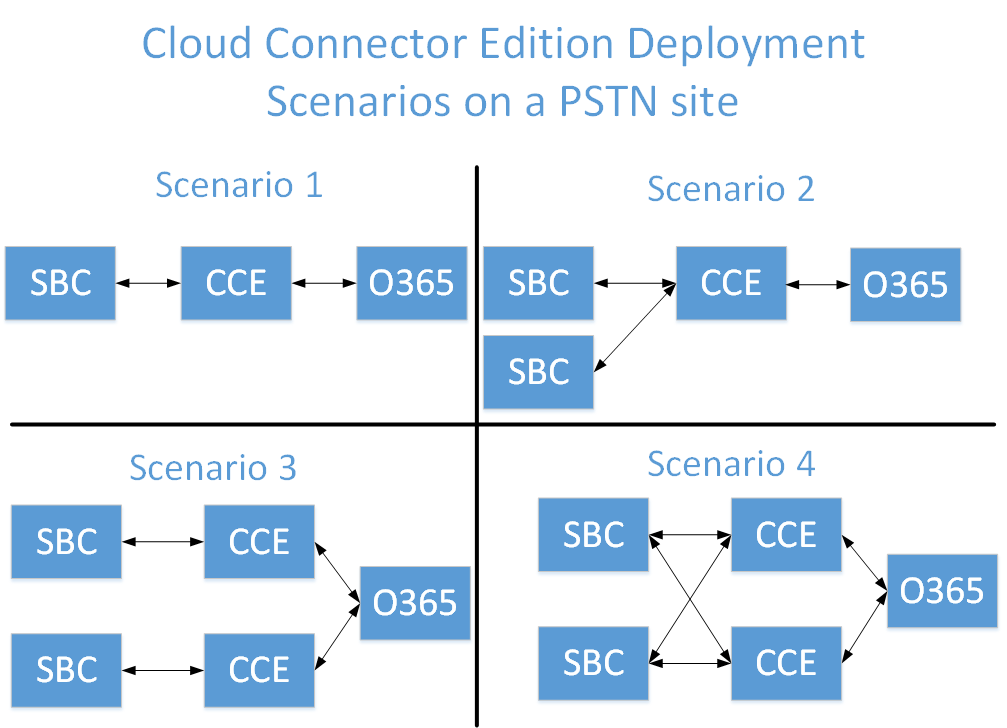
Before You StartCCE Deployment ScenariosThe following diagram shows typical CCE deployment scenarios on a PSTN site. The PSTN site is a combination of Cloud Connector instances, deployed at the same location, and with common PSTN gateways pool connected to them. PSTN sites allow you to: Provide connectivity to gateways that are closest to your users. Allow for scalability by deploying multiple Cloud Connector instances within one or more PSTN sites. Allow for high availability by deploying multiple instances of Cloud Connector within a single PSTN site.
| Caption |
|---|
| 0 | Figure |
|---|
| 1 | CCE Deployment Scenarios |
|---|
| 
|
|
Scenario 3 and Scenario 4 are covered in Configuring the SBC Edge for Two CCEs. This document contains steps for Scenario 1 and Scenario 2 deployments.
| Multiexcerpt |
|---|
| MultiExcerptName | PreRequisites |
|---|
|
Prerequisites| A public domain name prepared and mapped with your Office 365 tenant (for example, "mydomain.com"). See Create an Office 365 Tenant. | | An entry on your public domain name that points to the fixed IP address of your SBC Edge (for example, myccesite1.mydomain.com" with an IP address of "nn.nn.mm.nn"). | An Office 365 tenant with an E5 license or E3 + Cloud PBX. | You must have the Global Administrator role for your O365 tenant account. | A public certificate authority ready to sign a certificate for the SBC Edge. Important! Read the steps outlined in Certificate Requirements at Microsoft Technet. | A properly configured firewall. See Ports and Protocols at Microsoft Technet. | | Note |
|---|
| Latest System Release SBC Firmware and SbcComms Firmware
Important! - Refer to the SBC Edge Release Information page for instructions on obtaining the latest firmware.
- Failure to update to the latest firmware could lead to deployment failure.
- Make sure to use the latest sustaining release
|
|
| Note |
|---|
| Latest System Release SbcComms Firmware Important! - Refer to the SBC Edge Release Information page for instructions on obtaining the latest firmware.
- Failure to update to the latest firmware could lead to deployment failure.
- Make sure to use the latest sustaining release (use 6.1.2 rather than X.X.0, for example).
|
Microsoft Cloud Connector Edition image on ASM recovery partition. |
|
Network Settings
For this best practice, Cloud Connector Edition deployment follows the cabling shown below:
| Caption |
|---|
| 0 | Figure |
|---|
| 1 | Typical Deployments |
|---|
|
| | Microsoft Cloud Connector Edition image on ASM recovery partition. |
|
Network Settings
For this best practice, Cloud Connector Edition deployment follows the cabling shown below:
| Caption |
|---|
| 0 | Figure |
|---|
| 1 | Typical Deployments |
|---|
|
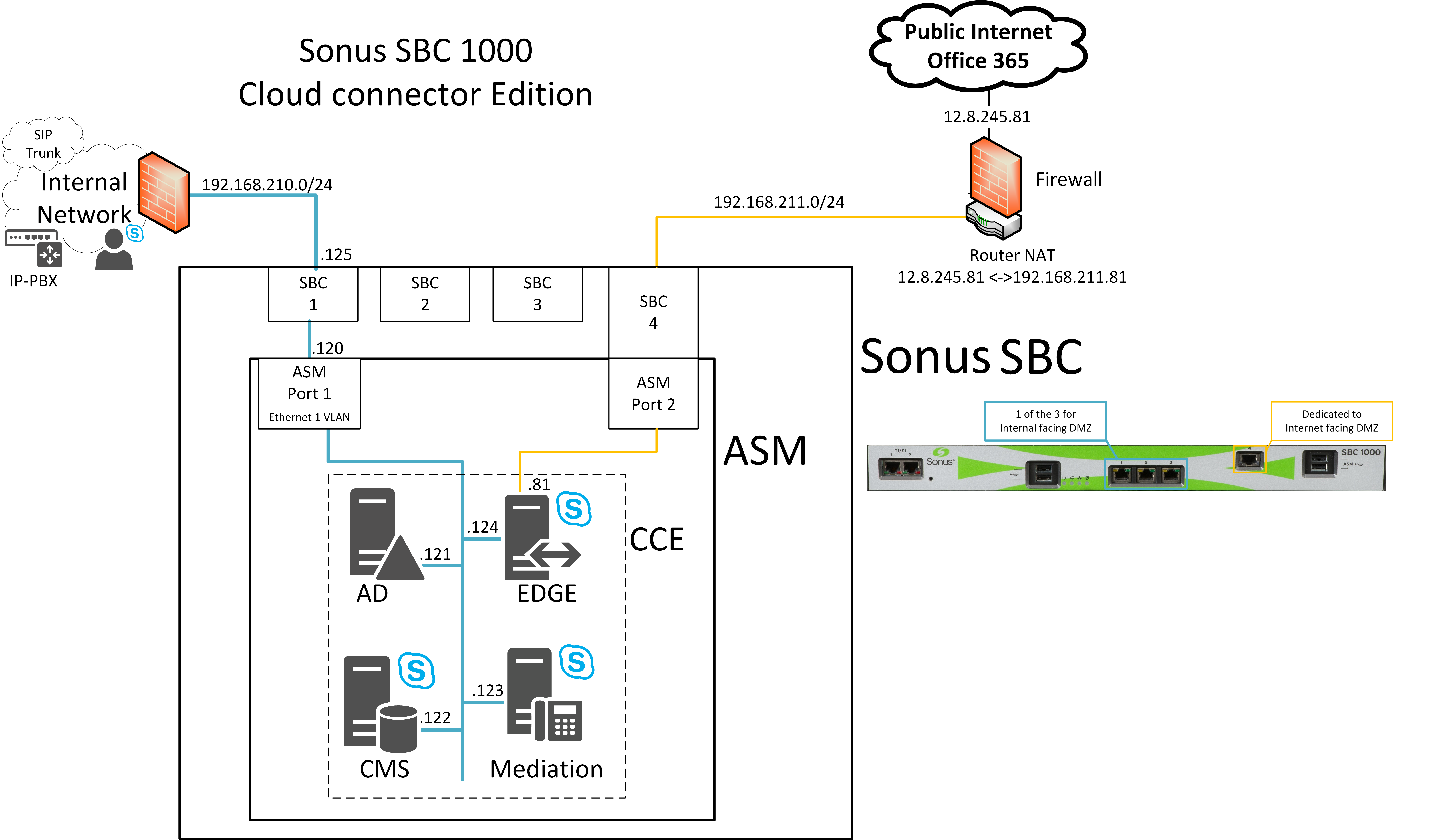 Image Added Image Added
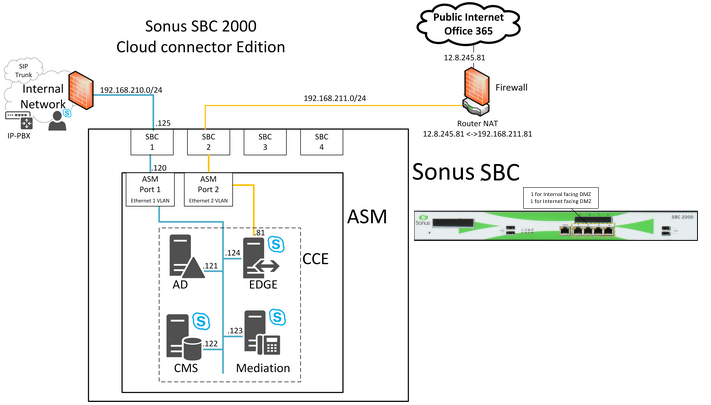 Image Added Image Added
|
Firewall Settings
For this best practice, the Router/Firewall is configured using the following rules:
 Image Removed
Image Removed
 Image Removed
Image RemovedFirewall Settings
For this best practice, the Router/Firewall is configured using the following rules:
| Caption |
|---|
| 0 | Table |
|---|
| 1 | Internal Firewall Rules |
|---|
|
| Source IP | Destination IP | Source Port | Destination Port |
|---|
Cloud Connector Mediation component | Internal clients | TCP 49 152 – 57 500* | TCP 50,000-50,019 (Optional) | Cloud Connector Mediation component | Internal clients | UDP 49 152 – 57 500* | UDP 50,000-50,019 | Internal clients | Cloud Connector Mediation component | TCP 50,000-50,019 | TCP 49 152 – 57 500* | Internal clients | Cloud Connector Mediation component | UDP 50,000-50,019 | UDP 49 152 -57 500* |
|
| Caption |
|---|
| 0 | Table |
|---|
| 1 | External Firewall Rules |
|---|
|
Source IP | Destination IP | Source Port | Destination Port |
|---|
Any | Cloud Connector Edge External Interface | Any | TCP 5061 | Cloud Connector Edge External Interface | Any | Any | TCP 5061 | Cloud Connector Edge External Interface | Any | Any | TCP 80 | Cloud Connector Edge External Interface | Any | Any | UDP 53 | Cloud Connector Edge External Interface | Any | Any | TCP 53 | Cloud Connector Edge External Interface | Any | TCP 50,000-59,999 | Any | Cloud Connector Edge External Interface | Any | UDP 3478 | Any | Cloud Connector Edge External Interface | Any | UDP 50,000-59,999 | Any | Any | Cloud Connector Edge External Interface | Any | TCP 443 | Any | Cloud Connector Edge External Interface | Any | TCP 50,000-59,999 | Any | Cloud Connector Edge External Interface | Any | UDP 3478 | Any | Cloud Connector Edge External Interface | Any | UDP 50,000 - 59,999 |
|
| Caption |
|---|
| 0 | Table |
|---|
| 1 | Host Firewall Rules - Internal or External Access |
|---|
|
| Source IP | Destination IP | Source Port | Destination Port |
|---|
| ASM | Any | Any | TCP 53 | | ASM | Any | Any | TCP 80 | | ASM | Any | Any | TCP 443 |
|
| Multiexcerpt |
|---|
| MultiExcerptName | DNSSettings |
|---|
|
DNS SettingsMake sure that CCE FQDN is resolving to the Public IP address. To do so, login to your DNS server and create the relevant entries. |
Preparing Your Node
Preparing the
for Initial Setup
Update the
firmware to the latest released version.
| Note |
|---|
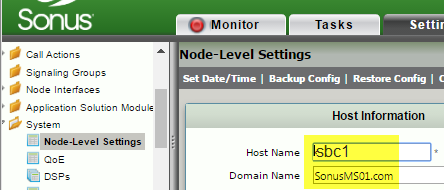
- Ensure the Node FQDN is definitive. Changing this information requires the CCE to be redeployed.
- Ensure that an NTP server is configured.
|
Sonus recommends Sonus recommends starting with a clean and empty configuration.
| Caption |
|---|
| 0 | Figure |
|---|
| 1 | Ensure That the Node FQDN is Correct |
|---|
|
|
| Info |
|---|
Optionally, if you want to configure a secondary in your environment, make sure to have the secondary network interface configured accordingly to be able to reach out to the internal company network (corporate network). |
Preparing the ASM
If your ASM have been used before, you should re-Initialize it now. Refer to Re-Initializing the ASM for details.
Confirm that the ASM is ready to deploy the Cloud Connector Edition. To do so:
| Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. |
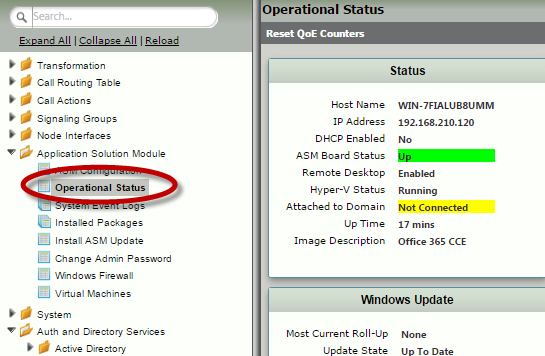
| 2 | Click the Task tab and then select Operational Status. |
| 3 | Verify the following:
ASM board Status is Up. Service Status is Running. The service version (SBC Communications Service) is the most recent version. If it is not, update it by following the steps in Installing an ASM Package.
|
| Caption |
|---|
| 0 | Figure |
|---|
| 1 | Operational Status |
|---|
|
|
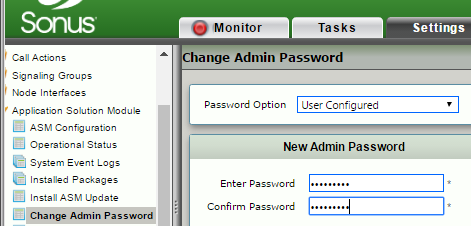
After you update the ASM, change its Admin Password.
| Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. |
| 2 | Click the Settings tab and then click Change Admin PasswordPassword. |
| 3 | Enter and confirm your new password and then click OK. |
| Caption |
|---|
| 0 | Figure |
|---|
| 1 | New Admin Password |
|---|
|
|
Deploying the CCE
Deploying the CCE on the
consists of two steps:
- Setup CCE using the WebUI.
- Prepare the CCE deployment on the WebUI using the Sonus Cloud Link Deployer.
Configuring the CCE using the SBC Edge WebUI
| Anchor |
|---|
| ConfiguringtheCCEthroughtheWebUI |
|---|
| ConfiguringtheCCEthroughtheWebUI |
|---|
|
Configuring the CCE Through the WebUI
ASM Config
| Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. |
| 2 | Navigate to Tasks > Setup Office 365 Cloud Connector Edition> Setup. |
| 3 | Click the ASM Config tab and configure/verify the Network and IP settings of your ASM. |
| 4 | Click Apply. After receiving the activity status as successfully completed, click the Generate CSR tab. |
| Caption |
|---|
|
 Image Removed Image Removed
|
Generating the CSR
This process is required only if you don't have a public certificate for your deployment. If you already have a certificate, proceed to Import Certificate.
| From the Remote Desktop Enabled drop down list, select Yes (to enable Remote Desktop) or No (to disable Remote Desktop). |
| 5 | From the Windows Firewall Enabled drop down list, select Yes (to enable Windows Firewall) or No (to disable Windows Firewall). |
| 6 | From the Proxy Enabled drop down list, Enables use of the Proxy Server on the ASM. Select from the drop down list: Yes (enables Proxy Server on the ASM) or No (disables Proxy Server). |
| 7 | From the Proxy Address drop down list, select Yes (to enable the IP address for the Proxy Server in IPv4 format). This field is available only when Proxy Enabled is set to Yes. |
| 8 | From the Proxy Port drop down list, select Yes (to enable the port in which the Proxy Server connects). Valid entry: Valid entry: 1 - 65000. This field is available only when Proxy Enabled is set to Yes. |
| 9 | Configure/verify the Network and IP settings of your ASM. |
| 10 | Click Apply. After receiving the activity status as successfully completed, click the Generate CSR |
| Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. |
| 2 | Navigate to Tasks > Setup Cloud Connector Edition > Generate CSR. |
| 3 | Generate the CSR as shown below with following information. To ensure creating a valid CSR for Cloud Connector Edition usage, please see the section "Certificate requirements" on https://technet.microsoft.com/en-us/library/mt605227.aspx. |
| 4 | Copy the CSR from the lower pane of the Generate CSR page and save it as a .txt file. |
| 5 | After the CSR is signed by the Certificate Authority and you receive the PKCS7 Certificate file, continue the wizard by clicking on Import Certificate tab. |
| Caption |
|---|
| 0 | Figure |
|---|
| 1 | Generate CSRASM Config |
|---|
|
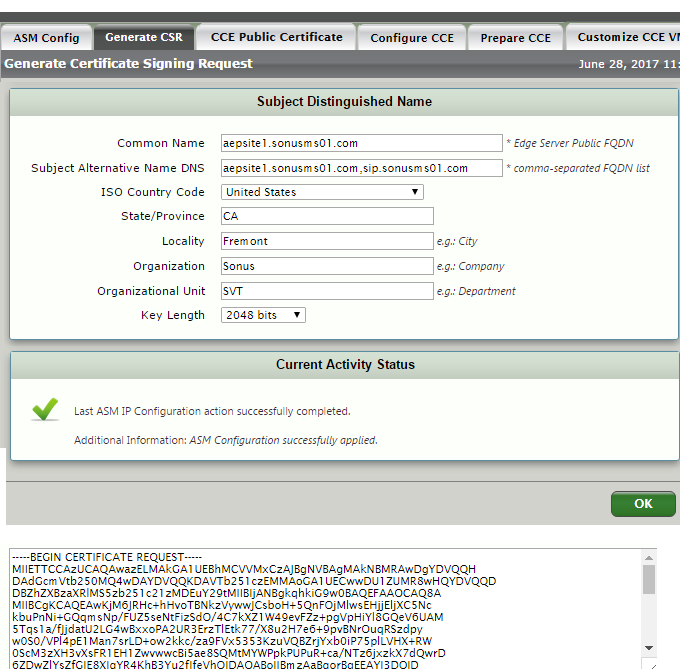 Image Removed Image Removed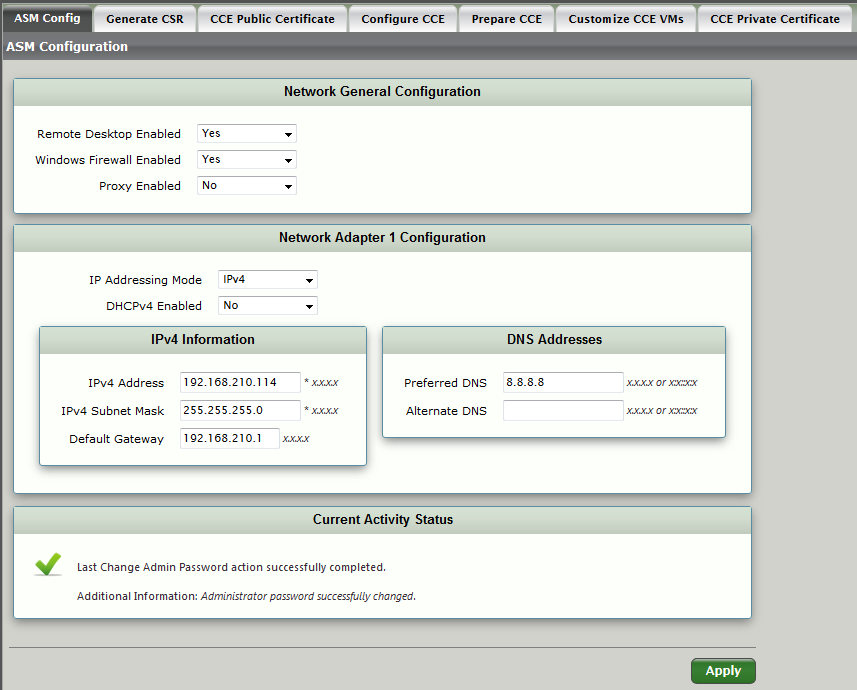 Image Added Image Added
|
| Anchor |
|---|
ImportCertificate | ImportCertificate | Importing Certificate/KeysGenerating the CSR
This process is required only if you don't have a public certificate for your deployment. If you already have a certificate, proceed to Import Certificate.
| Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. |
| 2 | Navigate to Tasks Tasks > Setup Office 365 Cloud Connector Edition and then click the Import Certificate/Keys tabEdition> Setup. |
| 3 | Click the Action drop-down list and select the appropriate option:- If you generated a Certificate Request (CSR) on the previous step, select the Import X.509 Signed Certificate option,
- If you prepare your certificate by yourself, select the Import PKCS12 Certificate and Key option. Enter the password for the certificate.
|
| 4 | Select the relevant certificate file using the Choose File button and then click OK. |
| 5 | Select the file by browsing to it using Select File. |
| 6 | Click OK. |
| 7 | After receiving the activity status as successfully completed, click on Configure CCE tab. |
| Generate CSR tab. |
| 4 | Generate the CSR as shown below with following information. To ensure creating a valid CSR for Cloud Connector Edition usage, please see the section "Certificate requirements" on https://technet.microsoft.com/en-us/library/mt605227.aspx. |
| 5 | Copy the CSR from the lower pane of the Generate CSR page and save it as a .txt file. |
| 6 | After the CSR is signed by the Certificate Authority and you receive the PKCS7 Certificate file, continue the wizard by clicking on CCE Public Certificate tab. |
| Caption |
|---|
|
 Image Added Image Added
|
| Anchor |
|---|
| ImportCertificate |
|---|
| ImportCertificate |
|---|
|
Set CCE Public Certificate| Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. |
| 2 | Open the Tasks tab and click Setup Navigate to Tasks > Office 365 Cloud Connector Edition in the navigation pane and click the CCE Public Certificate tab. |
| 3 | Click the Configure CCE tab. | 4 | Action drop-down list and select the appropriate option: - Import X.509 Signed Certificate. This option is used if you generated a Certificate Request (CSR) and this is the initial deployment. Paste the certificate in the window and click OK.
- Import PKCS12 Certificate and Key. Imports a certificate you created. Enter the password, select the file (certificate) to import, and click OK.
- Export PKCS12 Certificate and Key. Export the CCE certificate for backup purposes. Enter password and click OK.
- Transfer Public Certificate to Edge. Transfers the public certificate to the CCE (after deployment).
- Display Certificate. Displays the current SBC Edge certificate.
|
| 4 | After | Configure all necessary information and then click OK. All the pre-configured fields are valid as is, and recommended by Sonus. These fields may be edited, but all entries must meet Microsoft requirements.
| Warning |
|---|
If the deployment environment consists of multiple-site with a single certificate or a wild card certificate, ensure the CCE Site Name and the Edge Server Public Hostname are correct before proceeding. |
5 | After receiving the activity status as successfully completed, click the Prepare CCE tab to continueon Configure CCE tab. |
| Caption |
|---|
| 0 | Figure |
|---|
| 1 | Configure CCE Public Certificate |
|---|
|
 Image Added Image Added
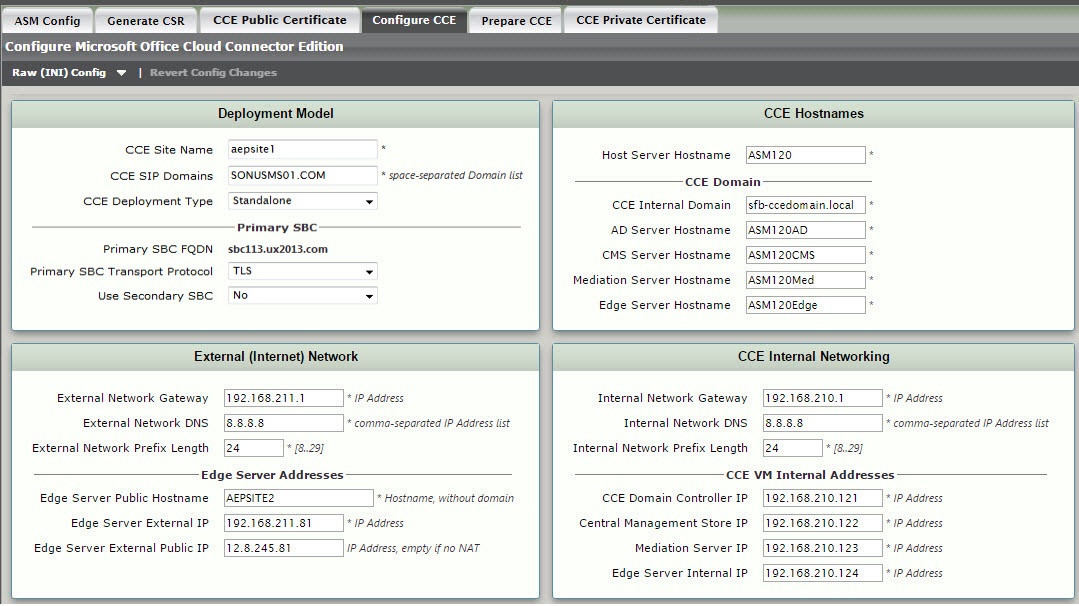 Image Removed Image Removed |
Preparing the CCE | Anchor |
|---|
Preparing the CCE | Preparing the CCE | | Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. |
| 2 | Open the Tasks tab and click Setup Cloud Connector Edition in the navigation pane. |
| 3 | Click the Prepare CCE tab. |
| 4 | Click the Prepare CCE button. A confirmation will request you to enter the password again for the new password. Only the Tenant credentials are already existing. Click OK as shown below. |
| Caption |
|---|
|
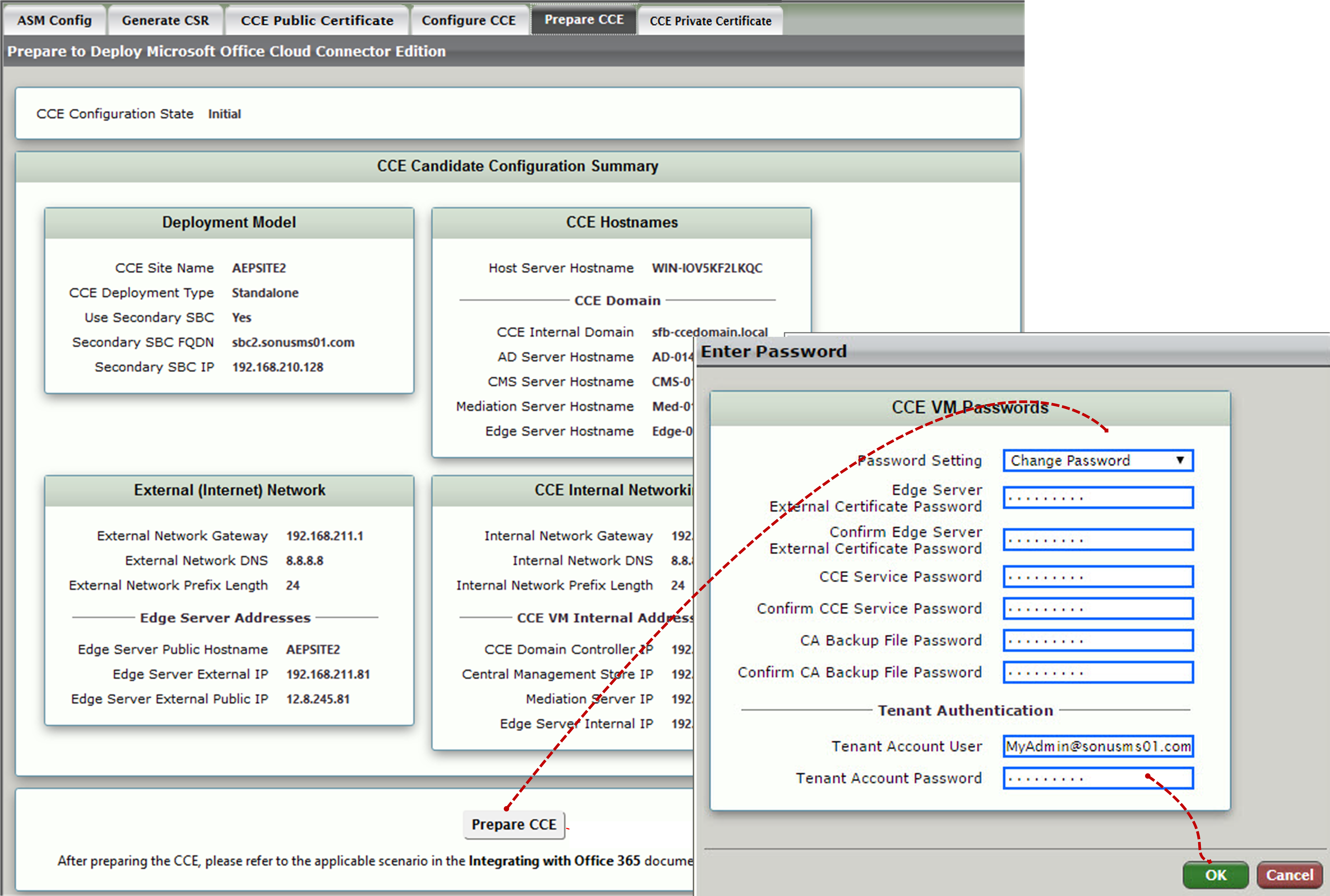 Image Removed Image Removed |
Activating the CCE
This step stores the two Microsoft product keys, and activates the CCE VM (which is not yet activated).
| Info |
|---|
The CCE requires four VMs; each Microsoft Product Key activates two VMs. |
| Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. |
| 2 | Open the Tasks tab and click Setup Cloud Connector Edition in the navigation pane. |
| 3 | Click the Activate CCE tab. |
| 4 | In Domain Controller and Central Management Store VM > Windows Product Key 1, enter the first Microsoft Product Key. To identify the Product Key, see Identify Microsoft Product Key. |
| 5 | In Under Mediation Server and Edge Server VM > Windows Product Key 2, enter the second Microsoft Product Key.To identify the Product Key, see Identify Microsoft Product Key. |
| 6 | Click Activate. |
| 7 | Access Tasks> Operational Status to verify Windows Activation. If activation fails, see Troubleshooting. |
| 8 | |
| Caption |
|---|
|
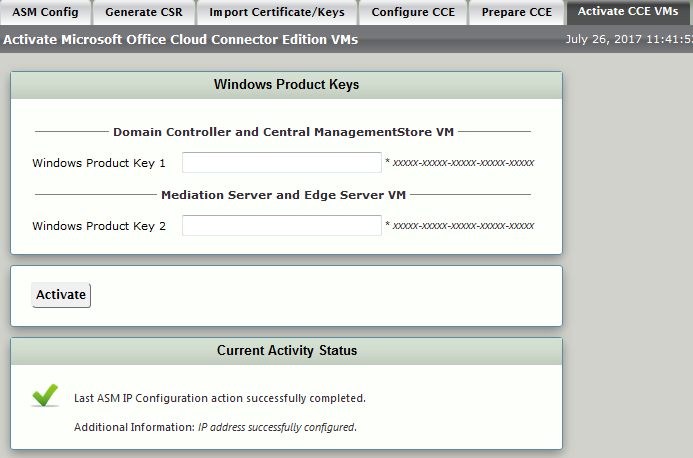 Image Removed Image Removed |
| Info |
|---|
| title | Identify Microsoft Product Key |
|---|
|
Configuring the CCE
| Note |
|---|
If you configure TLS and downgrade the system to a release prior to Release 7.0, the Exchange CA Certificate for TLS will be unavailable; you must re-deploy or upgrade to Release 7.0. Along with TLS configuration on the CCE, the TLS capability requires a loaded Root CA certificate and a signed certificate on the SBC. |
| Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. |
| 2 | Navigate to Tasks > Office 365 Cloud Connector Edition> Setup. |
| 3 | Click the Configure CCE tab. |
| 4 | Configure all necessary information and then click OK. All the pre-configured fields are valid as is, and recommended by Sonus. These fields may be edited, but all entries must meet Microsoft requirements. | Note |
|---|
TLS 1.2 is supported; the following fields are required to configure TLS: - Primary SBC Transport Protocol. Options: TCP or TLS (supports TLS 1.2).
- Secondary SBC Transport Protocol (optional). Options: TCP or TLS (supports TLS 1.2).
If TLS is configured as the Primary SBC Transport Protocol, you must run the Synchronize CCE/SBC CA Certificate task to allow a successful TLS handshake between CCE and SBC Edge. However, if TCP is configured as the Primary SBC Transport Protocol the Synchronize CCE/SBC CA Certificate task is not mandatory. See Managing Cloud Connector Edition Private Certificates. |
| Warning |
|---|
If the deployment environment consists of multiple-site with a single certificate or a wild card certificate, ensure the CCE Site Name and the Edge Server Public Hostname are correct before proceeding. |
|
| 5 | To increase Fast Failover (which shortens the time where certain ported numbers have a long delay from ITSP PSTN provider) configure Trunk Information: Refer Support. Indicates whether Gateways support Refer for a Call Transfer scenario. Valid entries: Enable (the Gateway(s) supports Refer which can handle call transfer) or Disable (the Gateway does not support Refer and the Mediation Server handles call transfer). Fast Failover Timer. Determines whether outbound calls that are not answered by the gateway within ten seconds will be routed to the next available trunk; if there are no additional trunks, the call will automatically be dropped. Valid entries: Enable or Disable. Forward Call History. Indicates whether call history information is forwarded through the trunk. Valid entries: Enable or Disable. Forward PAI. Indicates whether the P-Asserted-Identity (PAI) header will be forwarded along with the call. Valid entries: Enable or Disable. |
| 6 | After receiving the activity status as successfully completed, click the Prepare CCE tab to continue. |
| Caption |
|---|
|
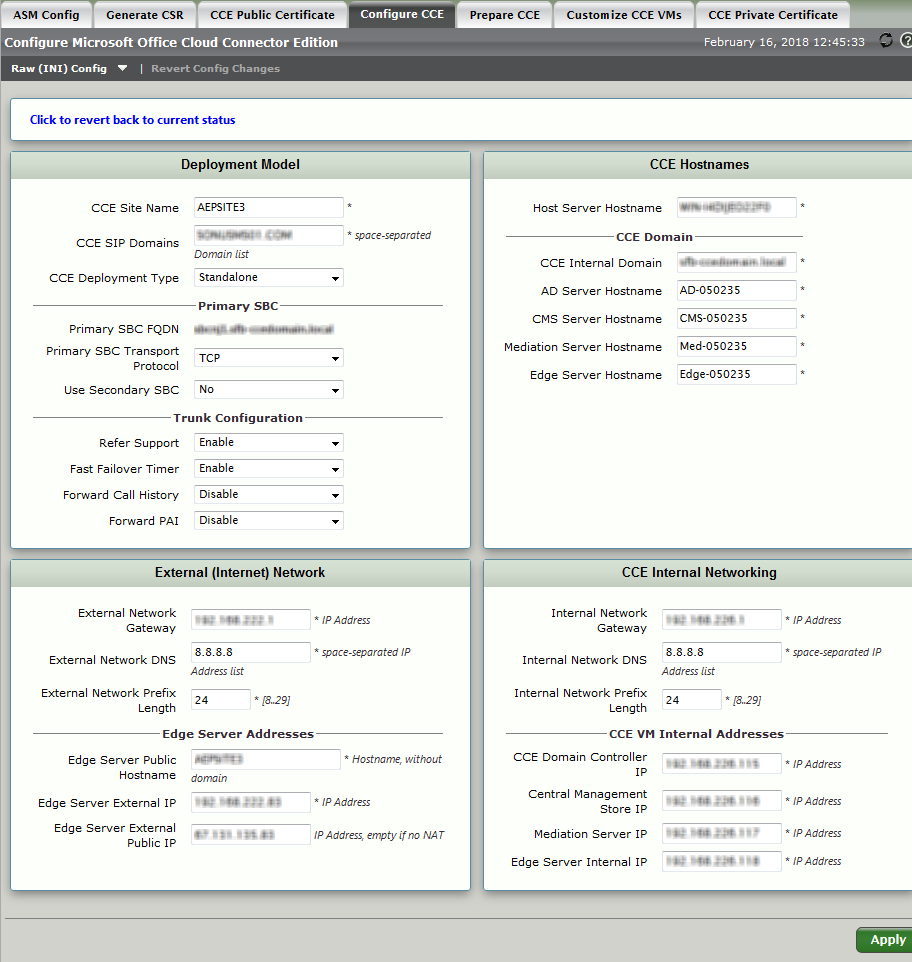 Image Added Image Added |
Preparing the CCE
| Anchor |
|---|
| Preparing the CCE |
|---|
| Preparing the CCE |
|---|
|
| Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. |
| 2 | Navigate to Tasks > Office 365 Cloud Connector Edition> Setup. |
| 3 | Click the Prepare CCE tab. |
| 4 | Click the Prepare CCE button. A confirmation will request you to enter the password again for the new password. Only the Tenant credentials are already existing. Click OK as shown below. |
| 5 | After confirmation, click on Customize CCE VMs. |
| Caption |
|---|
|
 Image Added Image Added |
Customizing the CCE VMs
This step stores the two Microsoft product keys, and customizes the CCE VM (which is not yet activated).
| Info |
|---|
The CCE requires four VMs; each Microsoft Product Key activates two VMs. |
| Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. |
| 2 | Navigate to Tasks > Office 365 Cloud Connector Edition> Setup. |
| 3 | Click the Customize CCE VMs tab. |
| 4 | In Domain Controller and Central Management Store VM > Windows Product Key 1, enter the first Microsoft Product Key. To identify the Product Key, see Identify Microsoft Product Key. |
| 5 | In Under Mediation Server and Edge Server VM > Windows Product Key 2, enter the second Microsoft Product Key.To identify the Product Key, see Identify Microsoft Product Key. |
| 6 | From the Proxy Usage drop down list, select Enabled (enables the Proxy Server on the DMZ facing the internal network) If you select Disable, the Proxy Server is disabled. |
| 7 | In the Proxy Server IP Address field, enter the server IP address for the Proxy Server in IPv4 format. This field is available only when Proxy Usage is set to Enabled. |
| 8 | In the Proxy Server Port field, enter the port number for the Proxy Server. Valid entry: 1 - 65535. This field is available only when Proxy Usage is set to Enabled. |
| 9 | Click Apply. |
| 10 | Access Tasks> Operational Status to verify Windows Activation. If activation fails, see Troubleshooting. |
| 11 | Click on CCE Private Certificate. |
| Caption |
|---|
| 0 | Figure |
|---|
| 1 | Customize CCE VMs |
|---|
|
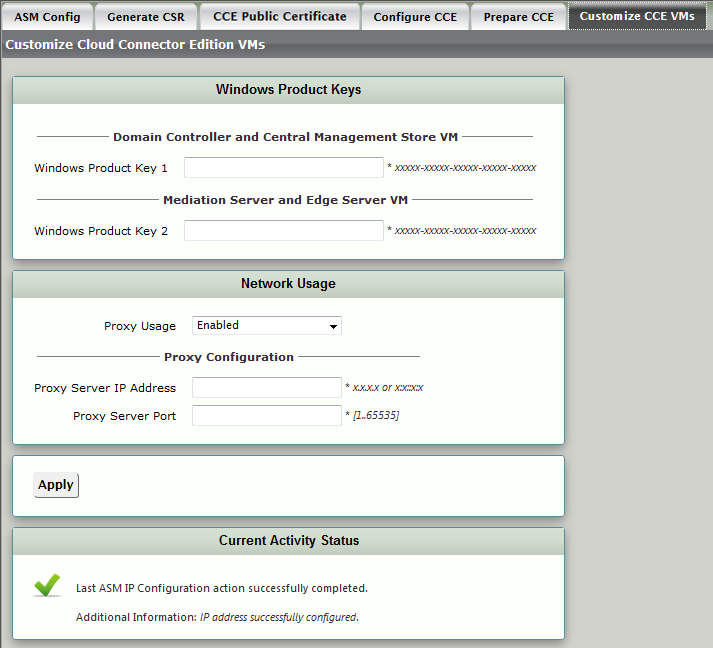 Image Added Image Added |
| Info |
|---|
| title | Identify Microsoft Product Key |
|---|
|
To identify the Microsoft Product Key:- Access the bottom of the SBC unit and locate the two Microsoft Certificate of Authenticity stickers.
- Locate the Microsoft Product Key for each.
Sample Microsoft Certificate of Authenticity Sticker
 Image Added Image Added
|
| Info |
|---|
| title | Activation - Troubleshooting Tips |
|---|
|
| Anchor |
|---|
| Troubleshooting |
|---|
| Troubleshooting |
|---|
|
If activation fails, check the following:- If access to the Microsoft Server fails, verify IP and Firewall configuration.
- Verify each Product Key has not reached the allowed limit of 15 activations.
- Verify correct entry of the Product Key.
|
Installing the CCE Appliance using Sonus Cloud Link Deployer| Note |
|---|
| title | CCE Deployment - What to Expect |
|---|
|
- The CCE deployment may exceed two hours.
- The CCE deployment status is visible only on the Remote Desktop to the ASM. The WebUI indicates that the CCE is running while the deployment process is in progress.
- While the CCE deployment is running, you should not perform any actions on the ASM via the WebUI (i.e., Shut Down/Reset/Reboot/Reinitialize/Install etc.).
- If the Office 365 PSTN Site already exists in your tenant, ensure the other Appliance is removed, and the CCE Auto-Update time window is properly configured. If you are in a time window dedicated to the Auto-Update, see Managing Update Schedule and Creating and Modifying PSTN Hybrid Site to configure the PSTN Hybrid Site and configure Auto-Update to false. Replication of the information may take up to 30 minutes.
|
| Step | Action |
|---|
| 1 | Remote desktop to the ASM system. |
| 2 | Launch the Sonus Cloud Link Deployer from icon on the desktop. |
| 3 | Check the first three actions:
- Transfer Password from SBC: This step imports the password that has been set during the Preparing the CCE.
- Register Appliance: This step registers this new appliance on your Office365 tenant.
- Install Appliance: This step deploys the CCE.
Select Apply. |
| Caption |
|---|
| 0 | Figure |
|---|
| 1 | Sonus Cloud Link Deployer |
|---|
|
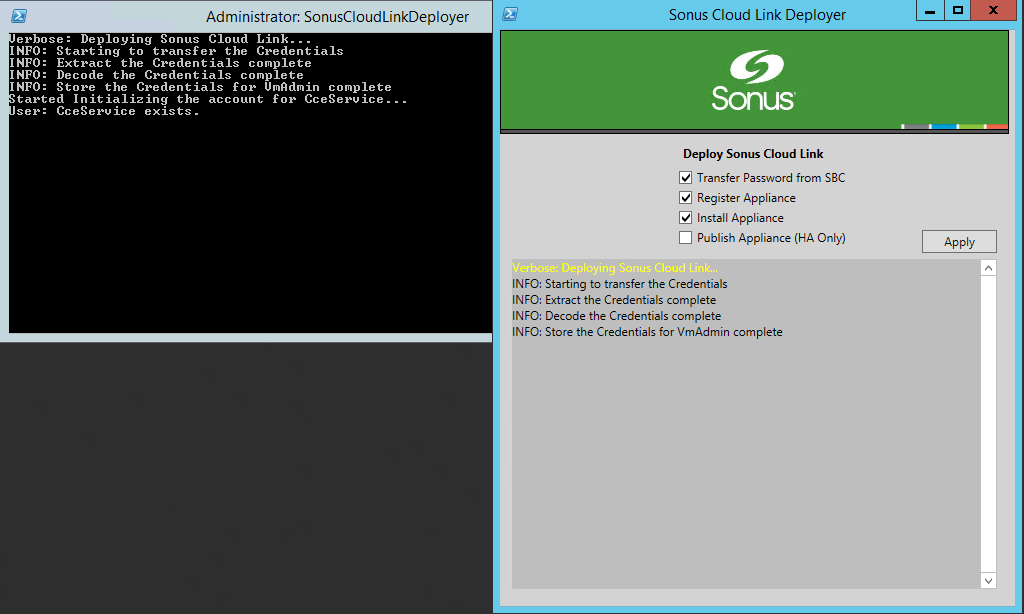 Image Added Image Added
|
Integrating the SBC Edge With Cloud Connector Edition
After the CCE is deployed, integrate the Sonus SBC Edge and allow calls from/to O365 clients. In this example, the following steps will set up the Sonus SBC Edge for:
SIP Provider (NNN.NNN.NNN.NNN) – SBC Edge (NNN.NNN.NNN.NNN) – CCE (mediation Server: NNN.NNN.NNN.NNN) – O365 Cloud
|
Build your SBC configuration
| Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. |
| 2 | Click the Tasks tab, and then click SBC Easy Setup > Easy Config Wizard in the navigation pane. |
| 3 | Follow steps 1, 2, and 3 as shown below and then click Finish. 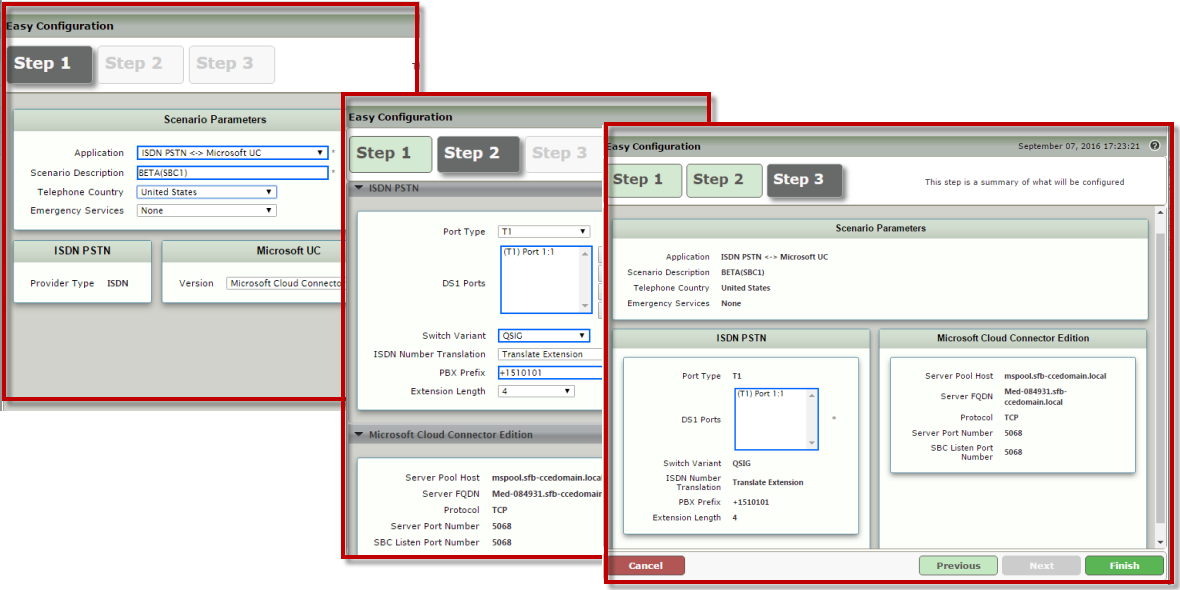 Image Added Image Added
|
| 4 | Click OK on the next two popups to complete the setup. |
| 5 | The wizard configures the necessary settings for the single SBC Edge and CCE integration. Relevant configuration items are shown in the Settings tab below: 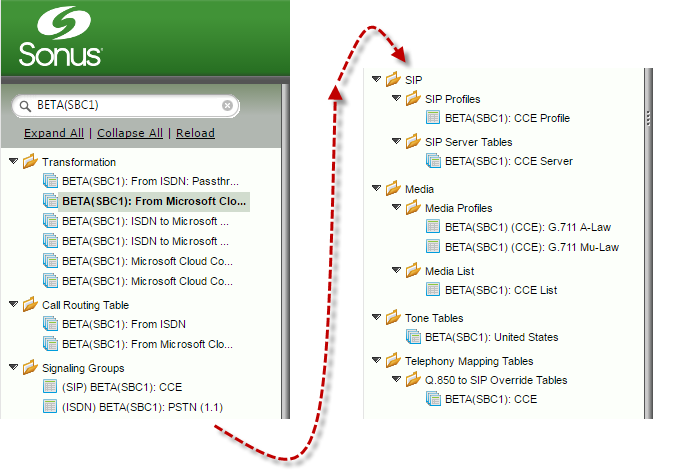 Image Added Image Added
|
Build your Second SBC Configuration (Optional)
| Anchor |
|---|
ProductKey | ProductKey | To identify the Microsoft Product Key:Access the bottom of the SBC unit and locate the two Microsoft Certificate of Authenticity stickers.Locate the Microsoft Product Key for each.Sample Microsoft Certificate of Authenticity Sticker Image Removed
Image Removed| Info |
|---|
| title | Activation - Troubleshooting Tips |
|---|
|
| Anchor |
|---|
Troubleshooting | Troubleshooting | If activation fails, check the following:- If access to the Microsoft Server fails, verify IP and Firewall configuration.
- Verify each Product Key has not reached the allowed limit of 15 activations.
- Verify correct entry of the Product Key.
| Anchor |
|---|
CCEAppliance | CCEAppliance | Installing the CCE Appliance using Sonus Cloud Link Deployer
| Note |
|---|
| title | CCE Deployment - Using a Proxy on the ASM Host |
|---|
|
If you plan to use a proxy on the ASM Host to reach Office 365, you must add the Management network (192.168.213.0) into the exclusion list and specify proxy settings per machine rather than per user. |
| Note |
|---|
| title | CCE Deployment - What to Expect |
|---|
|
- The CCE deployment may exceed two hours.
- The CCE deployment status is visible only on the Remote Desktop to the ASM. The WebUI indicates that the CCE is running while the deployment process is in progress.
- While the CCE deployment is running, you should not perform any actions on the ASM via the WebUI (i.e., Shut Down/Reset/Reboot/Reinitialize/Install etc.).
- If the Office 365 PSTN Site already exists in your tenant, ensure the other Appliance is removed, and the CCE Auto-Update time window is properly configured. If you are in a time window dedicated to the Auto-Update, you should use the command Set-CsHybridPSTNSite to set EnableAutoUpdate to $False. Replication of the information may take up to 30 minutes.
|
| Step | Action |
|---|
| 1 | Remote desktop to the ASM system. |
| 2 | Launch the Sonus Cloud Link Deployer from icon on the desktop. |
| 3 | Check the first three actions:
- Transfer Password from SBC: This step imports the password that has been set during the Preparing the CCE.
- Register Appliance: This step registers this new appliance on your Office365 tenant.
- Install Appliance: This step deploys the CCE.
Select Apply. |
| Caption |
|---|
| 0 | Figure |
|---|
| 1 | Sonus Cloud Link Deployer |
|---|
|
 Image Removed Image Removed
|
Integrating the SBC Edge With Cloud Connector Edition
After the CCE is deployed, integrate the Sonus SBC Edge and allow calls from/to O365 clients. In this example, the following steps will set up the Sonus SBC Edge for:
SIP Provider (NNN.NNN.NNN.NNN) – SBC Edge (NNN.NNN.NNN.NNN) – CCE (mediation Server: NNN.NNN.NNN.NNN) – O365 Cloud
|
| Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. |
| 2 | Click the Tasks tab, and then click SBC Easy Setup > Easy Config Wizard in the navigation pane. |
| 3 | Follow steps 1, 2, and 3 as shown below and then click Finish.  Image Removed Image Removed
|
| 4 | Click OK on the next two popups to complete the setup. |
| 5 | The wizard configures the necessary settings for the single SBC Edge and CCE integration. Relevant configuration items are shown in the Settings tab below:  Image Removed Image Removed
|
Build your Second SBC Configuration (Optional)
| Step | Action |
|---|
| 1 | Login to the WebUI of the Secondary SBC Edge. |
| 2 | Click the Tasks tab and then run the Easy Config. |
| 3 | The preceding step will configure the Secondary SBC Edge with the appropriate configuration items.
|
| the Secondary SBC Edge. |
| 2 | Click the Tasks tab and then run the Easy Config. |
| 3 | The preceding step will configure the Secondary SBC Edge with the appropriate configuration items.
|
| Multiexcerpt |
|---|
| MultiExcerptName | BasicCallVerification |
|---|
|
Basic Call Verification after CCE Deployment and IntegrationWith the preceding settings, an endpoint from the SIP provider side can dial the number of a Skype For Business (O365) client and reach out to it over . The call flow for this call is shown below: | Caption |
|---|
| 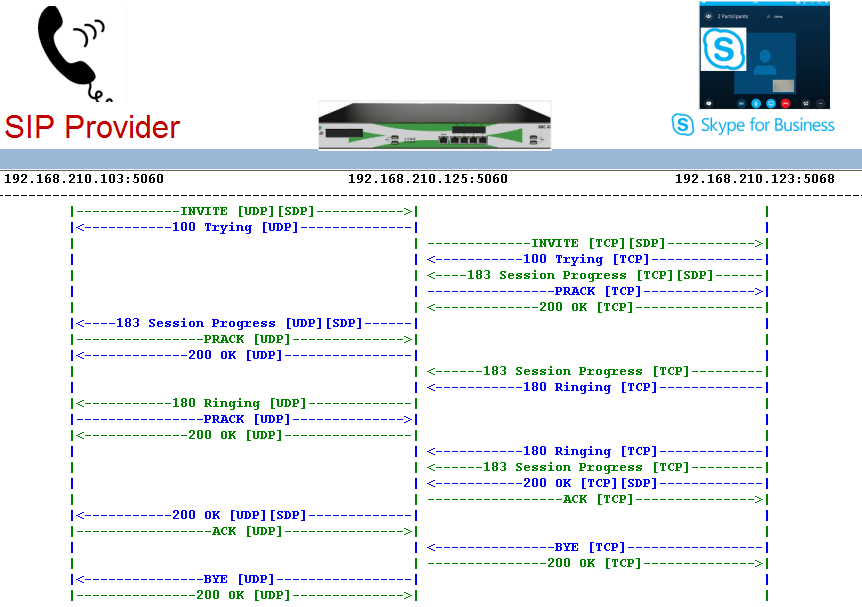 Image Added Image Added
|
Similarly, a Skype For Business (O365) client can dial the number of an endpoint off of ITSP and reach out to it over . The call flow for this call is shown below: | Caption |
|---|
| 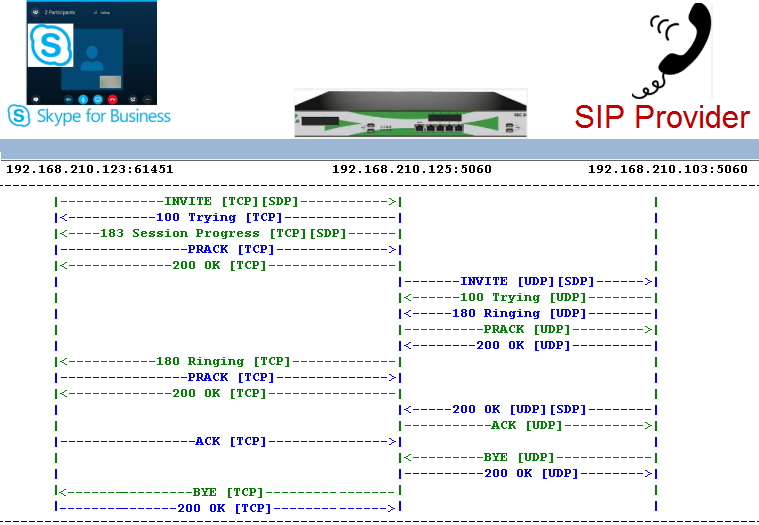 Image Added Image Added
|
|
| Multiexcerpt |
|---|
| MultiExcerptName | O365KnownIssues |
|---|
|
O365 Known Issue and Workarounds for CCERedeploying the CCE| Note |
|---|
Configuration changes to the CCE in the WebUI per Tasks > Setup Cloud Connector Edition> Configure CCE requires the CCE to be re-deployed. |
| Info |
|---|
Backup the Public Certificate per Tasks > Setup Cloud Connector Edition> Import Certificate. |
Clean Office 365 tenantIf the CCE was previously deployed, previously installed information must be cleared in O365. To do so, follow the steps below: | Step | Action |
|---|
| 1 | Remote Desktop to the ASM system | | 2 | Connect the Office365 Tenant through a series of commands as follows: a. Execute the following command: Import-Module skypeonlineconnector
$cred = Get-Credential
b. When prompted, execute the credentials for O365 Admin Tenant. c. Execute the following command: $Session = New-CsOnlineSession -Credential $cred -Verbose
Import-PSSession $session
| | 3 | Display all the Appliances assigned to your tenant, identify the Appliance you just re-initialized, and copy the identity into your clipboard.
Get-CsHybridPSTNAppliance
| | 4 | Execute the following command to remove the appliance: Unregister-CsHybridPSTNAppliance -Identity <paste the identity here> -Force
| | 5 | Execute the following command to verify that the appliance has been removed: Get-CsHybridPSTNAppliance
| | 6 | This completes the cleanup. |
Re-Initializing of the ASMThe ASM must be re-initialized with the image that contains the latest CCE software . To do so |
| Multiexcerpt |
|---|
| MultiExcerptName | BasicCallVerification |
|---|
|
Basic Call Verification after CCE Deployment and IntegrationWith the preceding settings, an endpoint from the SIP provider side can dial the number of a Skype For Business (O365) client and reach out to it over . The call flow for this call is shown below: | Caption |
|---|
|  Image Removed Image Removed
|
Similarly, a Skype For Business (O365) client can dial the number of an endpoint off of ITSP and reach out to it over . The call flow for this call is shown below: | Caption |
|---|
|  Image Removed Image Removed
|
|
| Multiexcerpt |
|---|
| MultiExcerptName | O365KnownIssues |
|---|
|
O365 Known Issue and Workarounds for CCERedeploying the CCE| Note |
|---|
Configuration changes to the CCE in the WebUI per Tasks > Setup Cloud Connector Edition> Configure CCE requires the CCE to be re-deployed. |
| Info |
|---|
Backup the Public Certificate per Tasks > Setup Cloud Connector Edition> Import Certificate. |
Clean Office 365 tenantIf the CCE was previously deployed, previously installed information must be cleared in O365. To do so, follow the steps below: | Step | Action |
|---|
| 1 | Remote Desktop Login to the ASM system | | 2 | Connect the Office365 Tenant through a series of commands as follows: a. Execute the following command: Import-Module skypeonlineconnector
$cred = Get-Credential
b. When prompted, execute the credentials for O365 Admin Tenant. c. Execute the following command: $Session = New-CsOnlineSession -Credential $cred -Verbose
Import-PSSession $session
| | 3 | Display all the Appliances assigned to your tenant, identify the Appliance you just re-initialized, and copy the identity into your clipboard.
Get-CsHybridPSTNAppliance
| | 4 | Execute the following command to remove the appliance: Unregister-CsHybridPSTNAppliance -Identity <paste the identity here> -Force
| | 5 | Execute the following command to verify that the appliance has been removed: Get-CsHybridPSTNAppliance
| | 6 | This completes the cleanup. |
Re-Initializing of the ASMThe ASM must be re-initialized with the image that contains the latest CCE software . To do so: | Step | Action |
|---|
| 1 | Login to the WebUI of the SBC Edge. | | 2 | Click the Task tab, and then click Reinitialize in the navigation pane. | | 3 | Select the appropriate image from the drop-down list and then click Apply. |
|
Manually Managing the CCE Configuration File
Editing the CCE Configuration File
The “.ini” file is the configuration of the Microsoft CCE (Cloud Connector Edition) running on the ASM. The contents of the ".ini" file must be as defined by Microsoft. From the Configure CCE panel, the Raw INI Config drop-down list enables you to edit, export, or import the ".ini" file.
Working with the ".ini" file allows you to provision multiple CCEs in a similar manner. Once you configure a CCE, you can export the ".ini" file, modify it for the second system, and then import the CCE. This procedure can then be repeated for the third system, etc. Also, backing up the SBC configuration and CCE configuration helps recover faster in the case of lost data.
| WebUI of the SBC Edge. | | 2 | Click the Task tab, and then click Reinitialize in the navigation pane. | | 3 | Select the appropriate image from the drop-down list and then click Apply. |
|
Manually Managing the CCE Configuration File
Editing the CCE Configuration File
The “.ini” file is the configuration of the Microsoft CCE (Cloud Connector Edition) running on the ASM. The contents of the ".ini" file must be as defined by Microsoft. From the Configure CCE panel, the Raw INI Config drop-down list enables you to edit, export, or import the ".ini" file.
Working with the ".ini" file allows you to provision multiple CCEs in a similar manner. Once you configure a CCE, you can export the ".ini" file, modify it for the second system, and then import the CCE. This procedure can then be repeated for the third system, etc. Also, backing up the SBC configuration and CCE configuration helps recover faster in the case of lost data.
| Step | Action |
|---|
| 1 | After receiving the activity status completion message, click the Click to re-configure CCE application button. |
| 2 | Click OK on the popup. |
| 4 | Click the Raw (INI) Config drop-down list, select Edit. Configurable fields are displayed for editing. Modifications to the CCE configuration requires redeployment of the CCE VM, and this action takes approximately two hours. Note: The example uses AEPSITE2 for the these attributes. |
| 5 | After verifying the information click OK. |
Importing and Exporting the CCE Configuration File
| |
|---|
| 1. |
| Step | Action |
|---|
1 | After receiving the activity status completion message, click the Click to re-configure CCE application button. |
| 2. | Click Click OK on on the popup.4 |
| 3. | Click From the Raw (INI) Config drop | - down list, | select Edit. Configurable fields are displayed for editing. Modifications to the CCE configuration requires redeployment of the CCE VM, and this action takes approximately two hours.Note: The example uses AEPSITE2 for the these attributes.
| 5 | After verifying the information click OK. |
Importing and Exporting the CCE Configuration File
select Import or Export. - Export. Exports the .ini file.
- Import. Imports the .ini file.
|
Updating the CCE Password
Follow these steps if you need to update the O365 tenant admin password or account.
| Step | Action |
|---|
| 1.After receiving | the activity status completion message, click the Click to re-configure CCE application button On the WebUI, click Tasks and select the Prepare CCE tab (see Preparing the CCE). |
| 2. | Click OK on the popup Prepare CCE. |
| 3 | . | From the | Raw (INI) Config Password Setting drop down list | , select Import or Export.- Export. Exports the .ini file.
- Import. Imports the .ini fil
| , select Change Password. Keep the same passwords for the Edge Server, CCE Service and CA Backup File, but change the passwords for Tenant Account User and Tenant Account Password. |
| 4 | On Remote desktop, start the Sonus Cloud Link Deployer, and check Transfer Password from SBC to reset the credentials. |
Renew CCE Public Certificate
Follow these steps to renew the CCE Public Certificate.
Follow these steps if you need to update the O365 tenant admin password or account.
| Step | Action |
|---|
| 1 | On the WebUI, run Preparing the CCE to specify a new Password. Select the existing password and enter the new password. Only the O365 should be modified for a running instance of CCE. |
| 2 | On Remote desktop, start the Sonus Cloud Link Deployer, and check Transfer Password from SBC to reset the credentials. |
| click Tasks and select the Generate CSR. |
| 2 | Sign the certificate with your public CA. |
| 3 | Import the new certificate into the Public Certificate tab. |
| 4 | Transfer the Certificate to the SBC Edge using the Public Certificate tab. |



















